A Deep dive into Cybersecurity
Cybersecurity refers to a set of techniques used to protect the integrity of networks, programs and data from attack, damage or unauthorized access.
From a computing point of view, security comprises cybersecurity and physical security — both are used by enterprises to protect against unauthorized access to data centers and other computerized systems. Information security, which is designed to maintain the confidentiality, integrity, and availability of data, is a subset of cybersecurity. The use of cyber security can help prevent cyber attacks, data breaches, and identity theft and can aid in risk management.
So when talking about cybersecurity, one might wonder “What are we trying to protect ourselves against?” Well, there are three main aspects we are trying to control, name:
- Unauthorized Access
- Unauthorized Deletion
- Unauthorized Modification
These three terms are synonymous with the very commonly known CIA triad which stands for Confidentiality, Integrity, and Availability. The CIA triad is also commonly referred to as the three pillars of security and most of the security policies of an organization are built on these three principles.
The CIA Triad
The CIA triad which stands for Confidentiality, Integrity, and Availability is a design model to guide companies and organizations to form their security policies. It is also known as the AIC triad to avoid confusion with the Central Intelligence Agency(CIA). The components of the triad are considered to be the most important and fundamental components of security. So let me brief you all about the three components
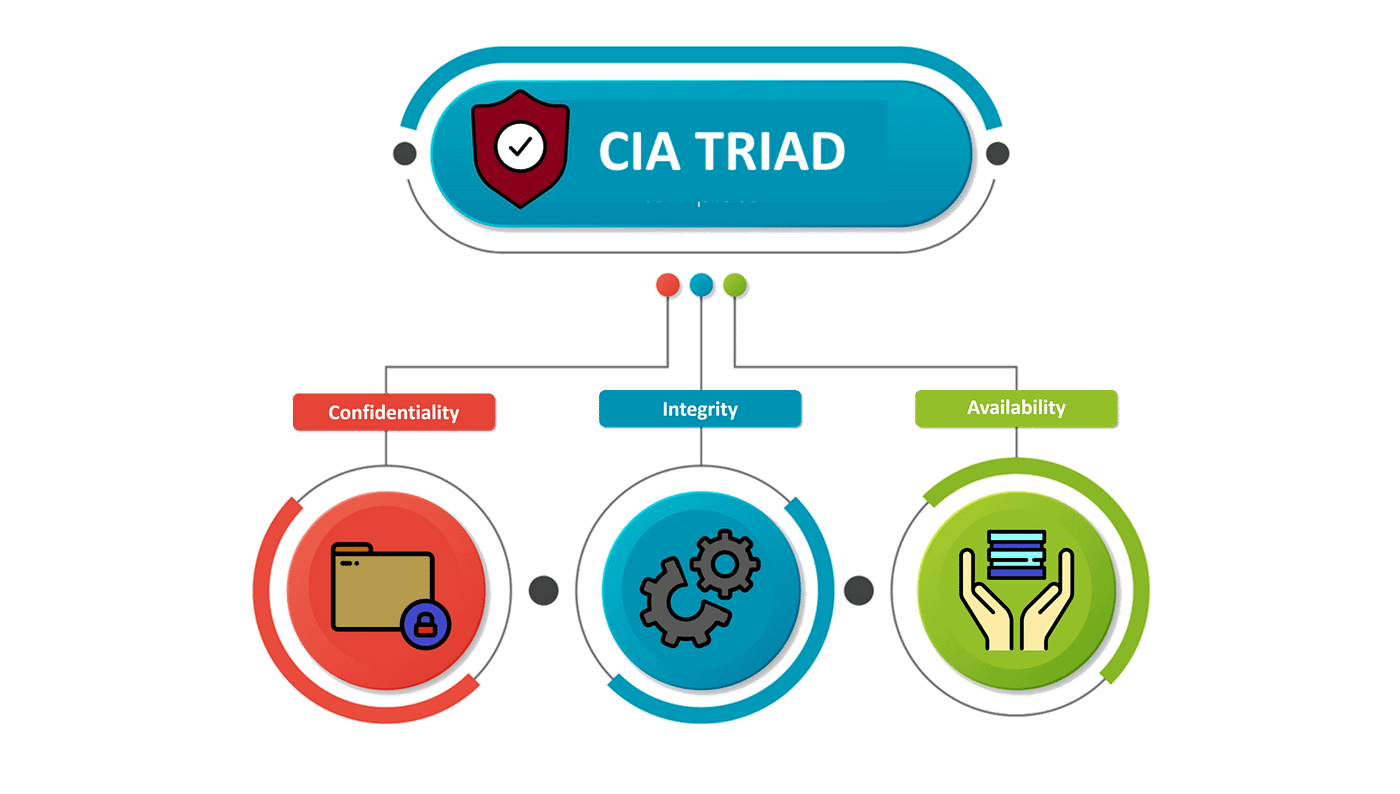
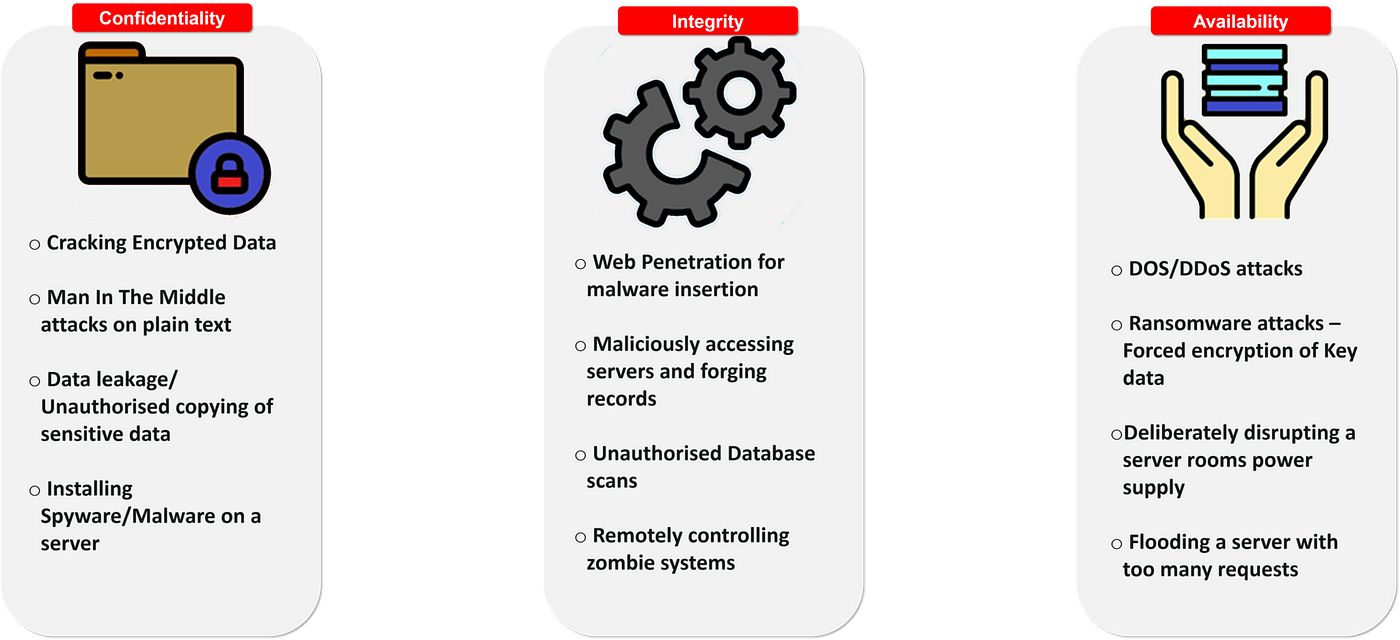
Confidentiality
Confidentiality is the protection of personal information. Confidentiality means keeping a client’s information between you and the client, and not telling others including co-workers, friends, family, etc.
Integrity
Integrity, in the context of computer systems, refers to methods of ensuring that data is real, accurate and safeguarded from unauthorized user modification.
Availability
Availability, in the context of a computer system, refers to the ability of a user to access information or resources in a specified location and in the correct format.
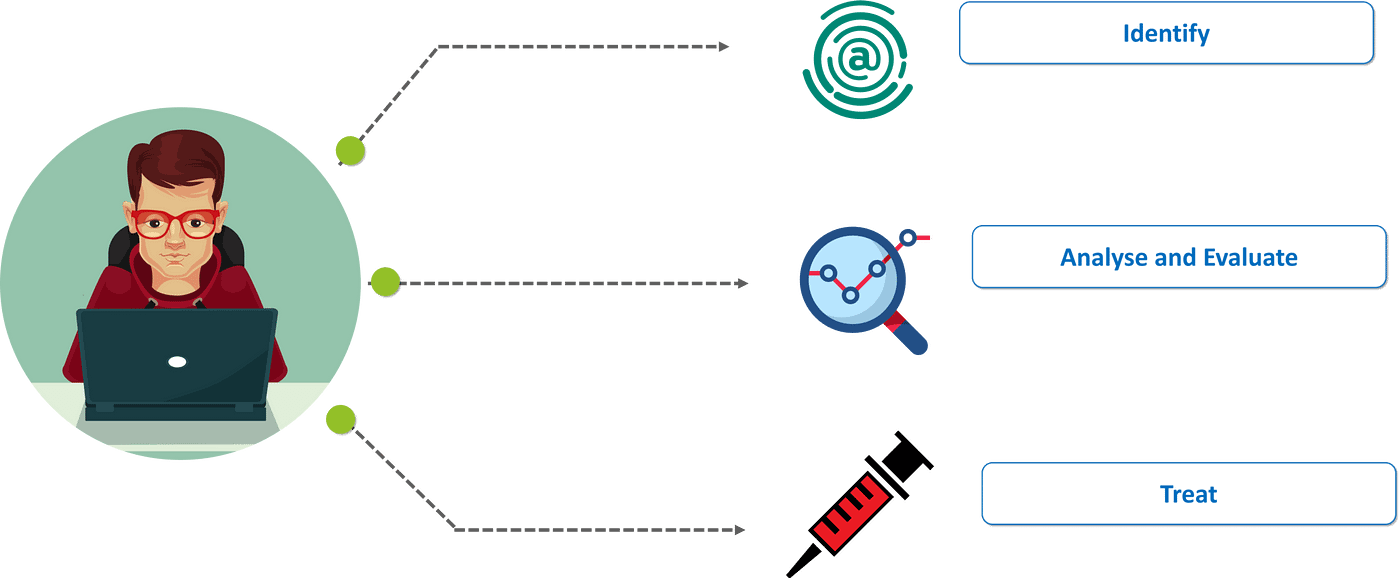
How is Cybersecurity implemented?
There are numerous procedures for actually implementing cybersecurity, but there three main steps when actually fixing a security-related issue.
The first step is to recognize the problem that is causing the security issue, for example, we have to recognize whether there is a denial of service attack or a man in the middle attack. The next step is to evaluate and analyze the problem. We have to make sure we isolate all the data and information that may have been compromised in the attack. Finally, after evaluating and analyzing the problem, the last step is to develop a patch that actually solves the problem and brings back the organization to a running state.
When identifying, analyzing and treating a cyber attack, there are three principals that are kept in mind for various calculations. They are:


Comments
Post a Comment